Configure Personal Access Token#
Let's add a few secrets that we will need to get our pipelines running. You can check secrets documentation to read more on these secrets.
Objectives#
- Generate a organization level PAT with the necessary permissions for pipeline integration.
- Securely store the GitHub PAT in Vault for added protection.
Key Results#
- Personal Access Token (PAT) with the specified permissions is generated successfully in the GitHub account.
- The GitHub PAT is securely stored in Vault and can be accessed only by authorized entities, enhancing security.
Prerequisites#
- Infra GitOps Repository is configured.
- Delivery Engineer added as the owner of root-tenant.
- Delivery Engineer added as a member of customer admin group. The customer admin group provides permission to deploy ArgoCD application in ArgoCD namespace.
- A GitHub user with access over all the repositories on GitHub. You can name this user
saap-bot.
Tutorial#
Creating Personal Access Token#
-
Generate a Fine-grained Token (PAT) on GitHub.
-
Go to your GitHub account
settingsfor the top-right corner on your profile. -
Navigate to
Developer settings -
Go to
Personal access tokens. -
From drop-down select
Fine-grained Tokens. -
Click
Generate new token. -
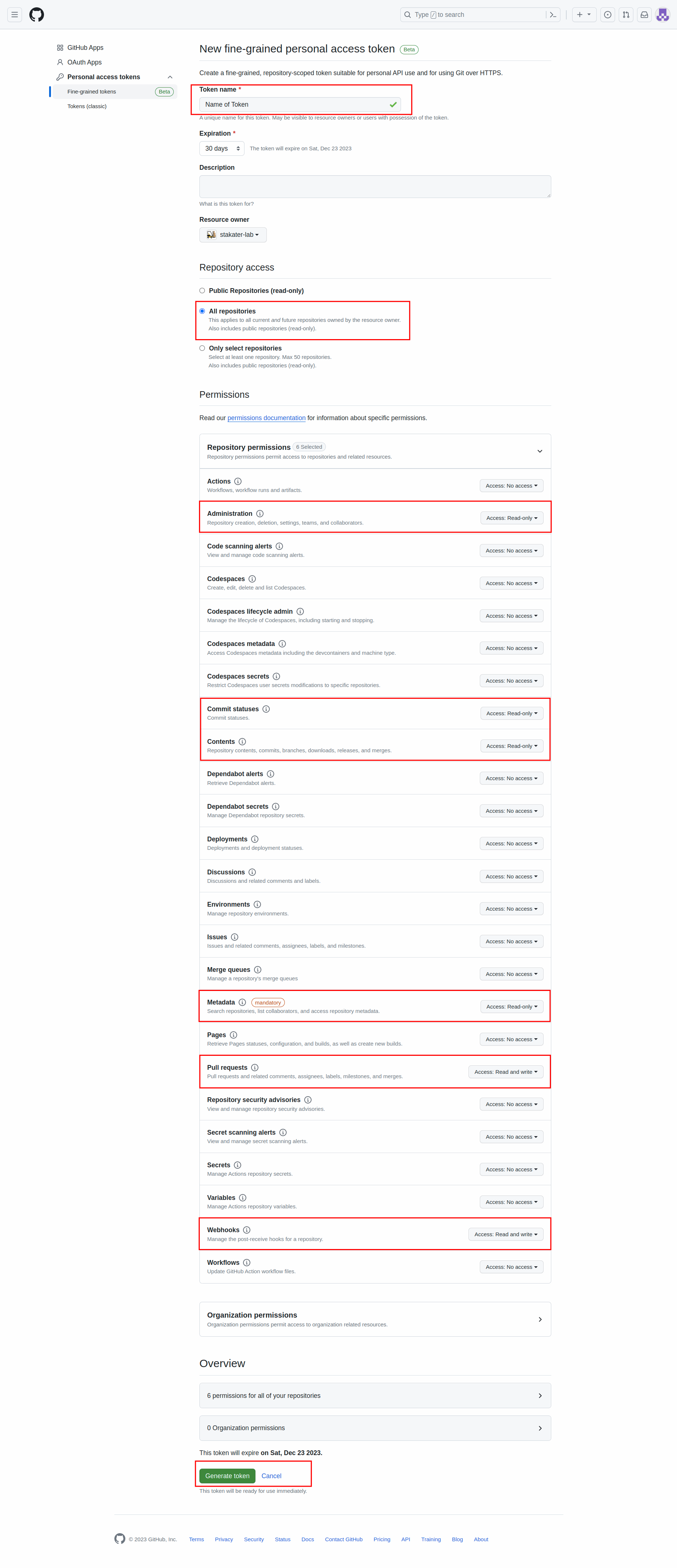
Provide a name for the token.
-
Select the
Resource owner(your organization). -
Set Repository Access to
All Repositories. -
Select the following scopes/permissions:
* Administration (Read only) * Commit status (Read only) * Contents (Read only) * Metadata (Read only) * Pull requests (Read and write) * Webhook (Read and write)
Note
Save the token cautiously, you'll need to save it in Vault.
Adding Token to Vault#
Now that we have created the GitHub Token, we will store it in Vault.
Note
The delivery engineer should be part of the root-tenant. The root tenant makes sure that the delivery engineer is able to login to Vault with OIDC and is able to view the ArgoCD application created for bootstrapping Infra repository. Please contact SAAP team if you are unable to access Vault using OIDC method
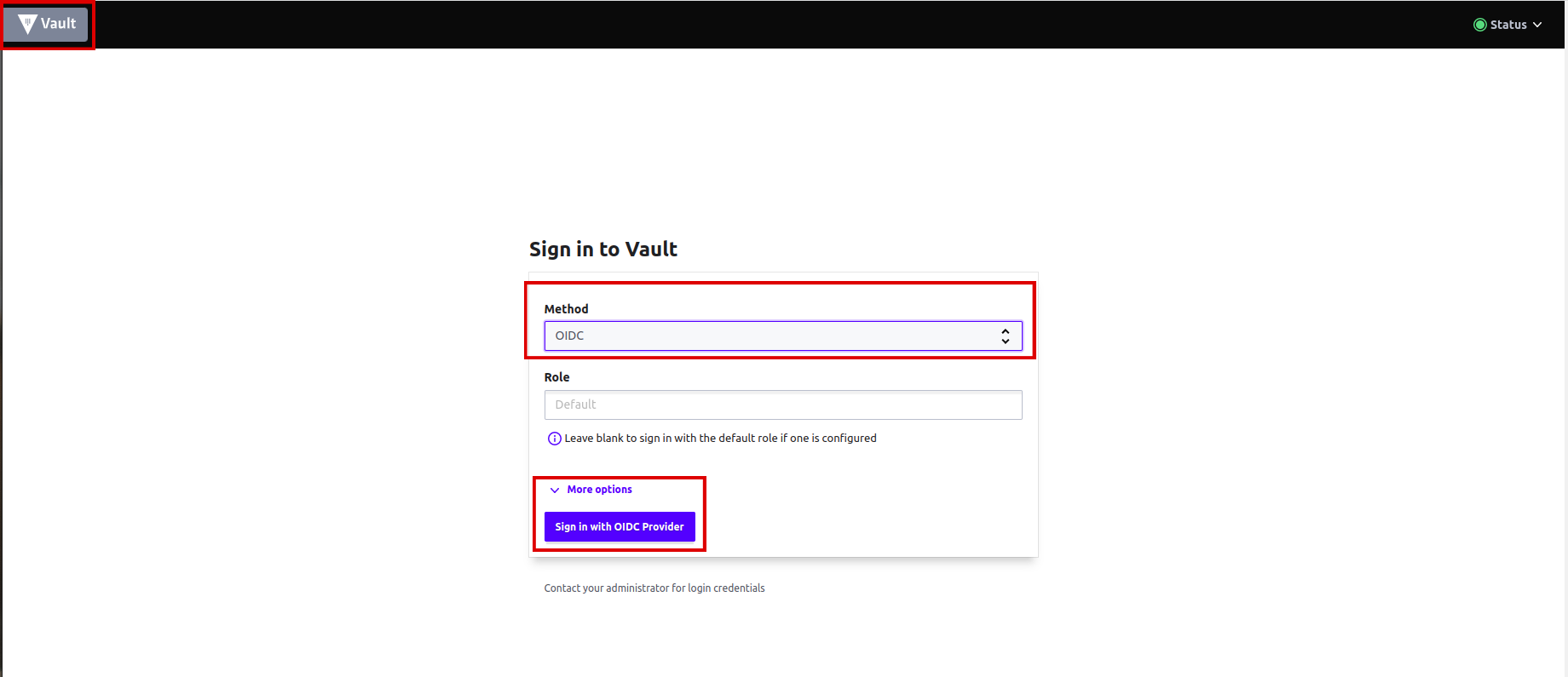
Login to Vault to view
-
Access Vault from
Forecastleconsole, searchVaultand open theVaulttile. -
From the drop-down menu under
Method, selectOIDCand click onSign in with OIDC Provider. -
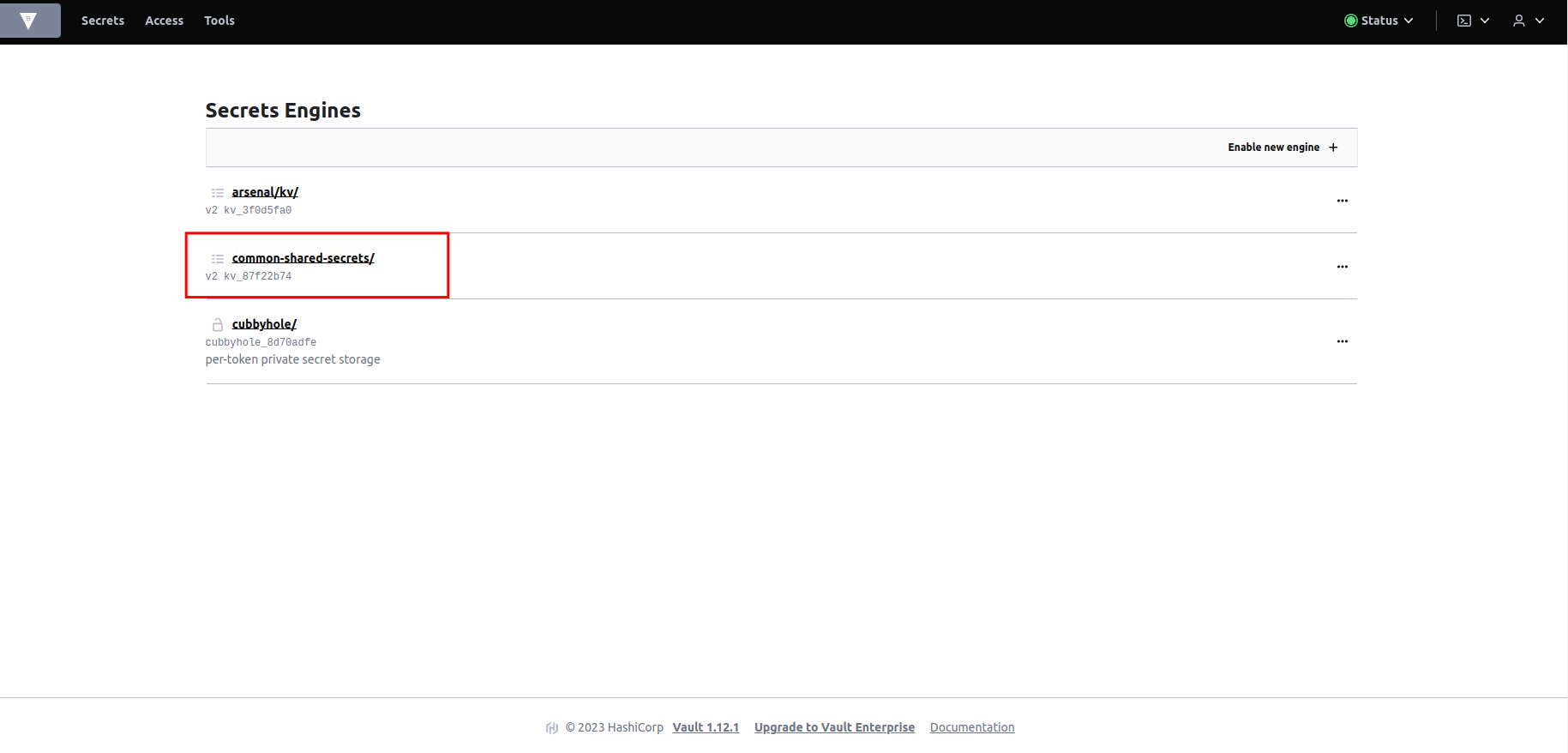
You will be brought to the
Vaultconsole. You should seecommon-shared-secretsfolder. -
Click on
common-shared-secrets. -
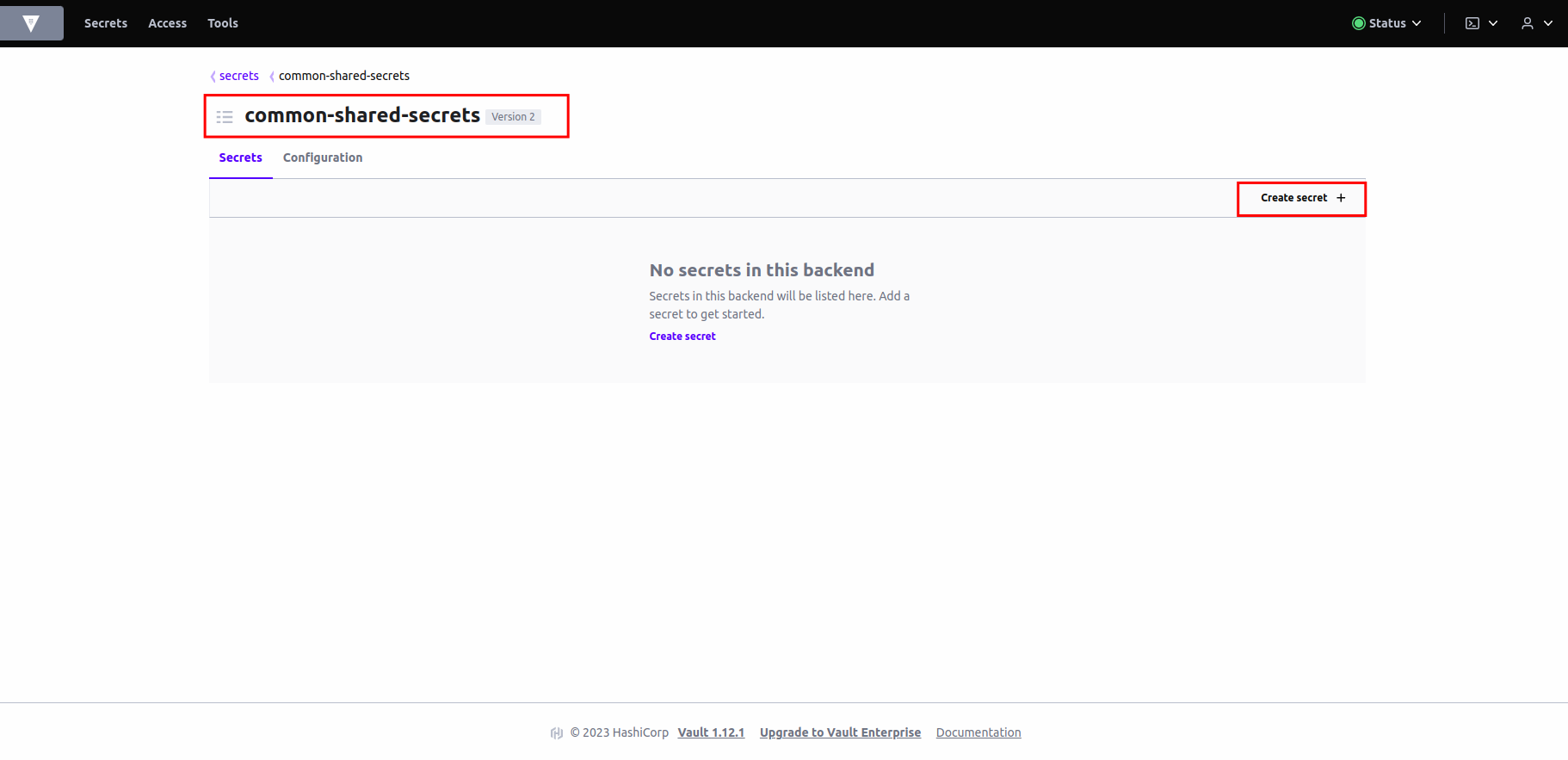
You will now be brought to the
secretsand theconfigurations. Click oncreate secret. -
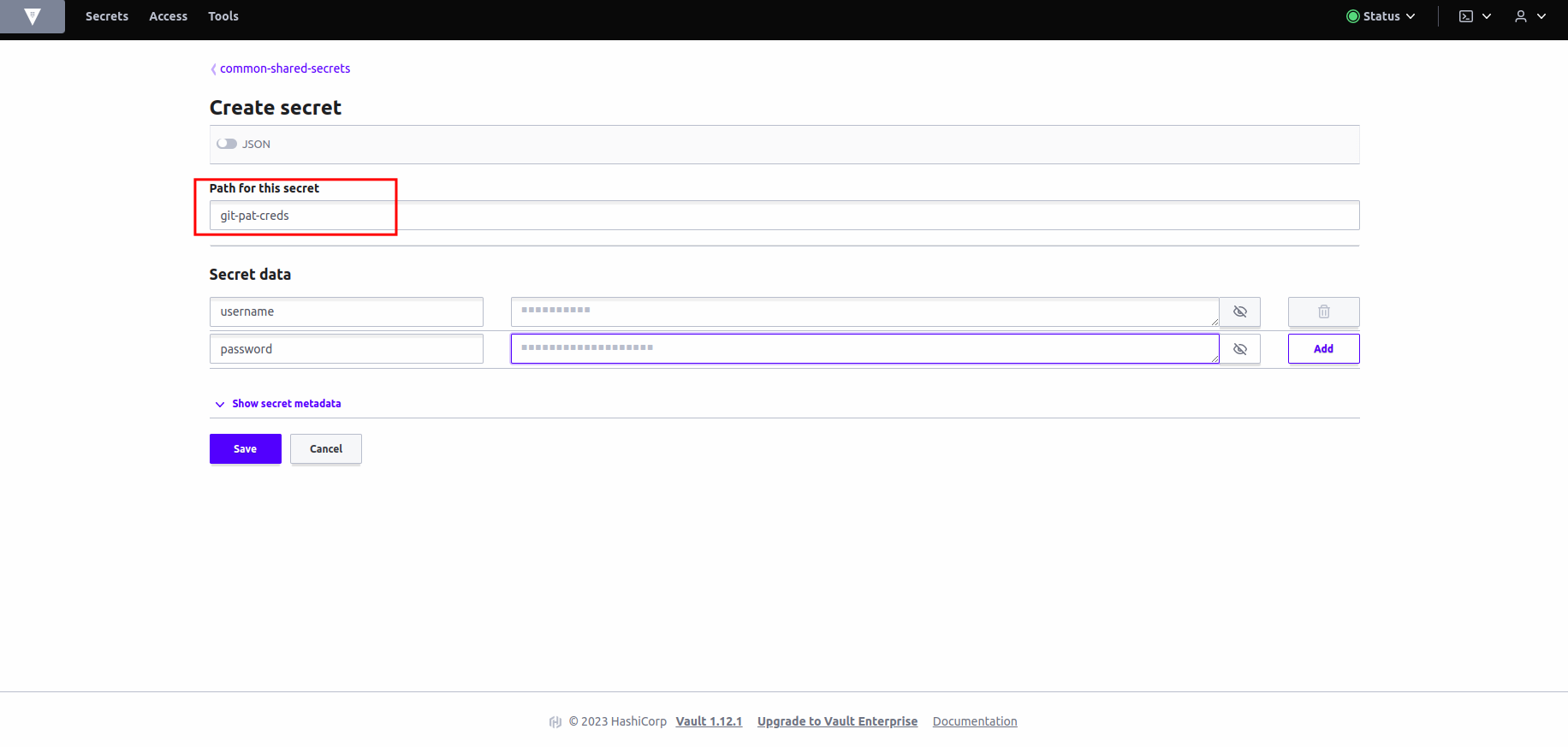
Let's create a
git-pat-credssecret for our webhook secret. Write the name of the secret inpathwhich isgit-pat-creds. Addsecret data- key:
username, value: (GitHub username). - key:
password, value (Newly created PAT). Hit save.
- key:
Adding External Secret#
Since we want the git-pat-creds secret to be deployed in all of the tenant namespaces, we will use a multi-tenant-operator template to deploy it.
-
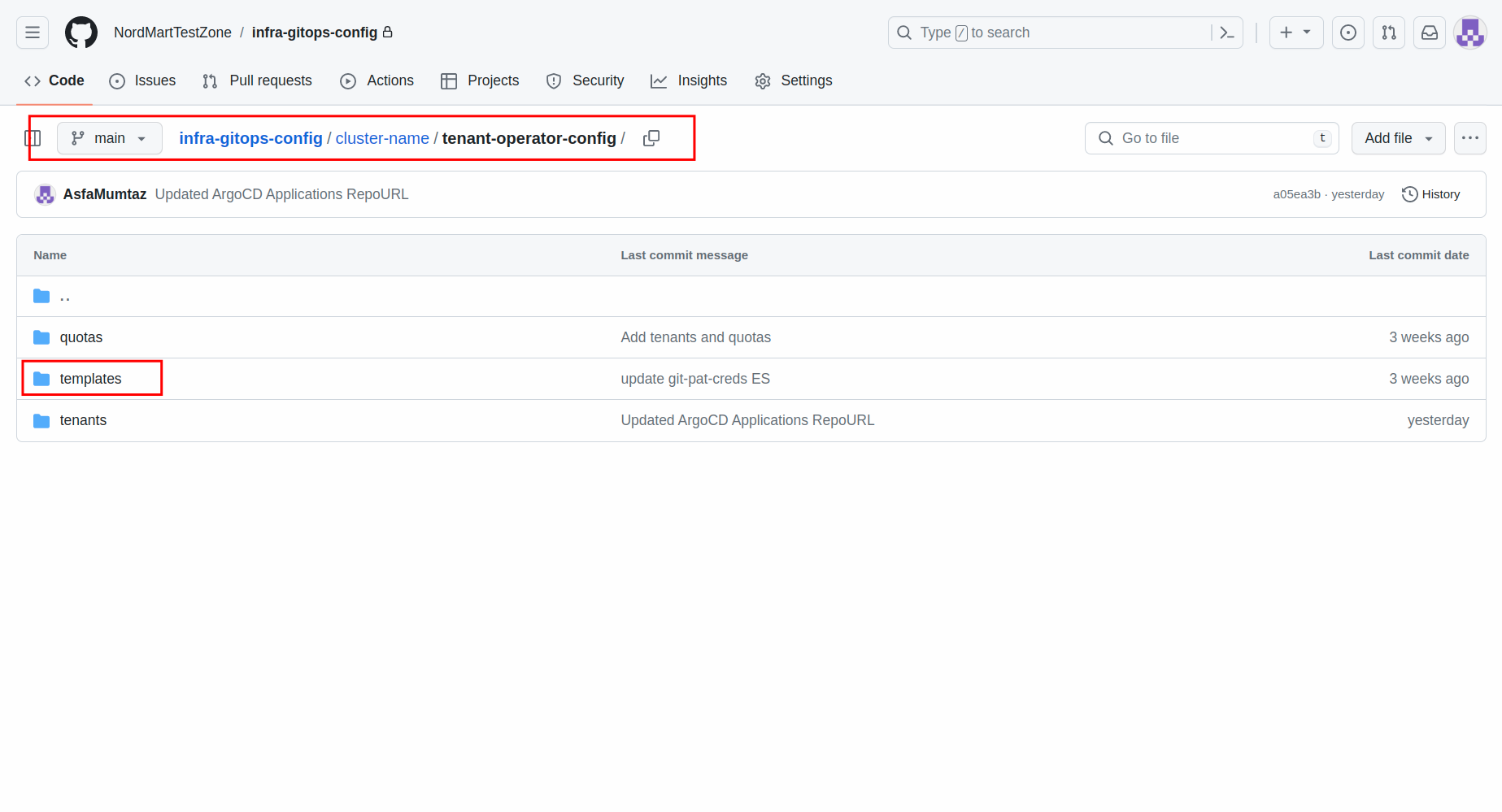
Open up the
infra-gitops-configrepository that we have already bootstrapped. -
Open the
tenant-operator-configfolder and create atemplatesfolder inside it. -
Now create a file named
git-pat-creds-template.yamland add the following content.apiVersion: tenantoperator.stakater.com/v1alpha1 kind: Template metadata: name: git-pat-creds resources: manifests: - apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata: name: git-pat-creds spec: dataFrom: - extract: conversionStrategy: Default key: git-pat-creds refreshInterval: 1m0s secretStoreRef: kind: SecretStore name: tenant-vault-shared-secret-store target: name: git-pat-creds -
Create another file named
git-pat-creds-tgi.yamland add the below content. -
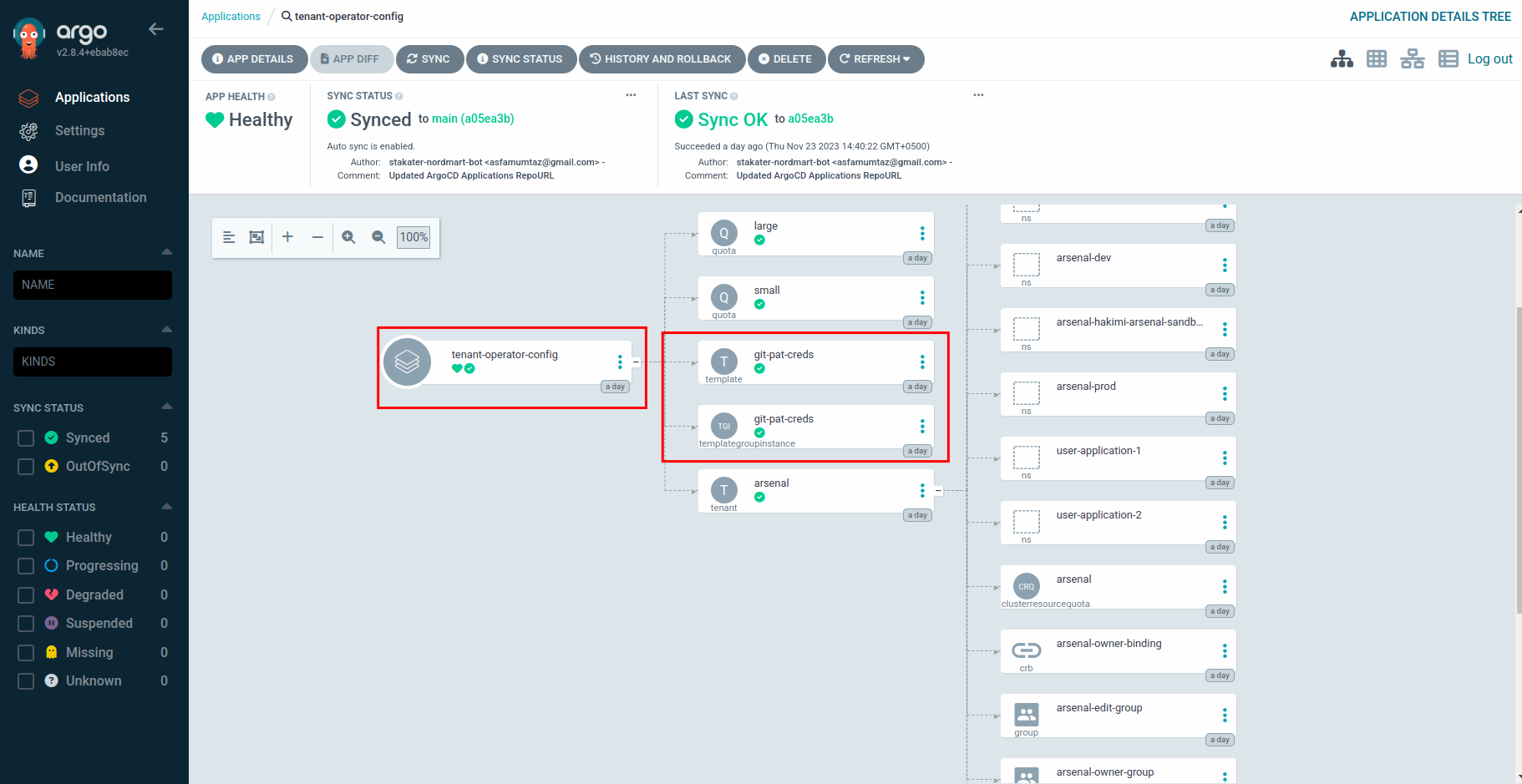
Lets see our Template and TGI in ArgoCD. Open up ArgoCD and look for
tenant-operator-configapplication. You should be able to see your Template and TGI deployed.