Configure SSH Key#
Objectives#
- Generate a organization level SSH keypair.
- Securely store the keypair in Vault for added protection.
Key Results#
- SSH keypair with read write access is generated.
- Public key is stored in SCM (GitHub)
- SSH key is securely stored in Vault and can be accessed only by authorized entities, enhancing security.
Prerequisites#
- Infra GitOps Repository is configured.
- A User that has access to all the repositories in your SCM organization/group.
Tutorial#
Creating SSH keypair#
-
Generate an ssh keypair. You can follow the official GitHub documentation for this.
Note
Save the keypair cautiously, you'll need to add it to Vault and GitHub.
-
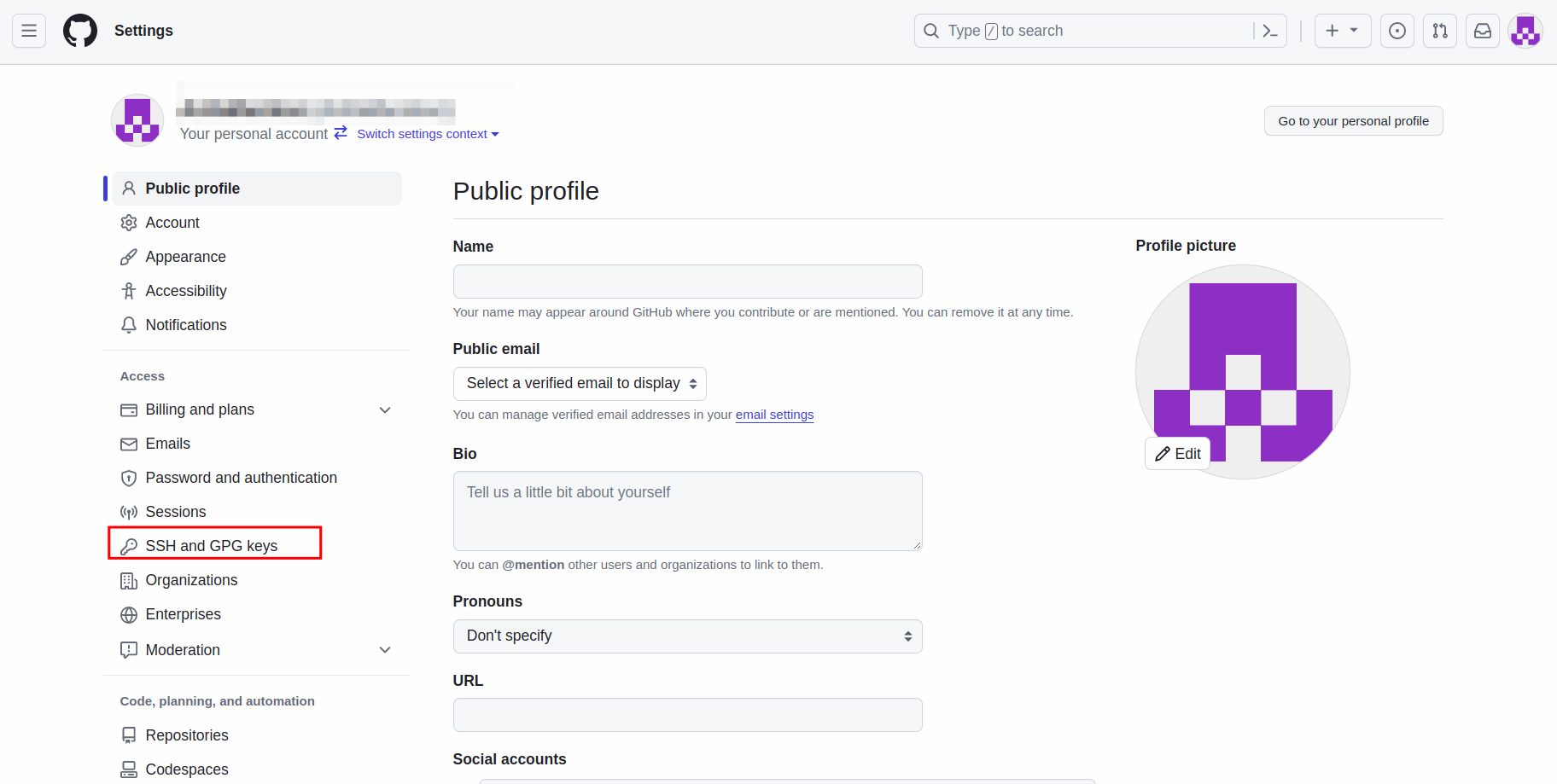
Once you've generated the keypair, go to your GitHub account
settingsfor the top-right corner on your profile. -
Navigate to
SSH and GPG Keys -
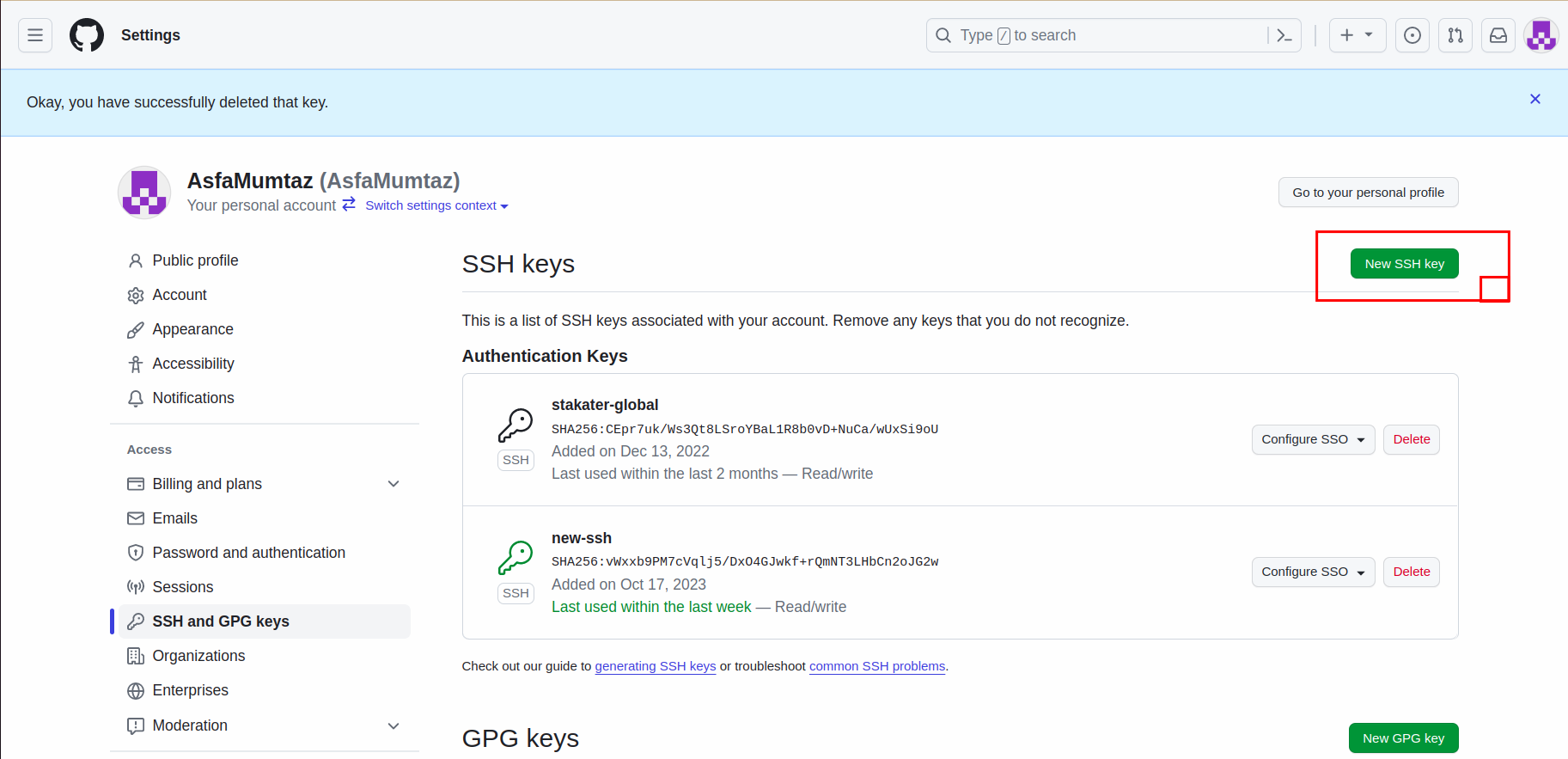
Click
Add New Keyin SSH Key section. -
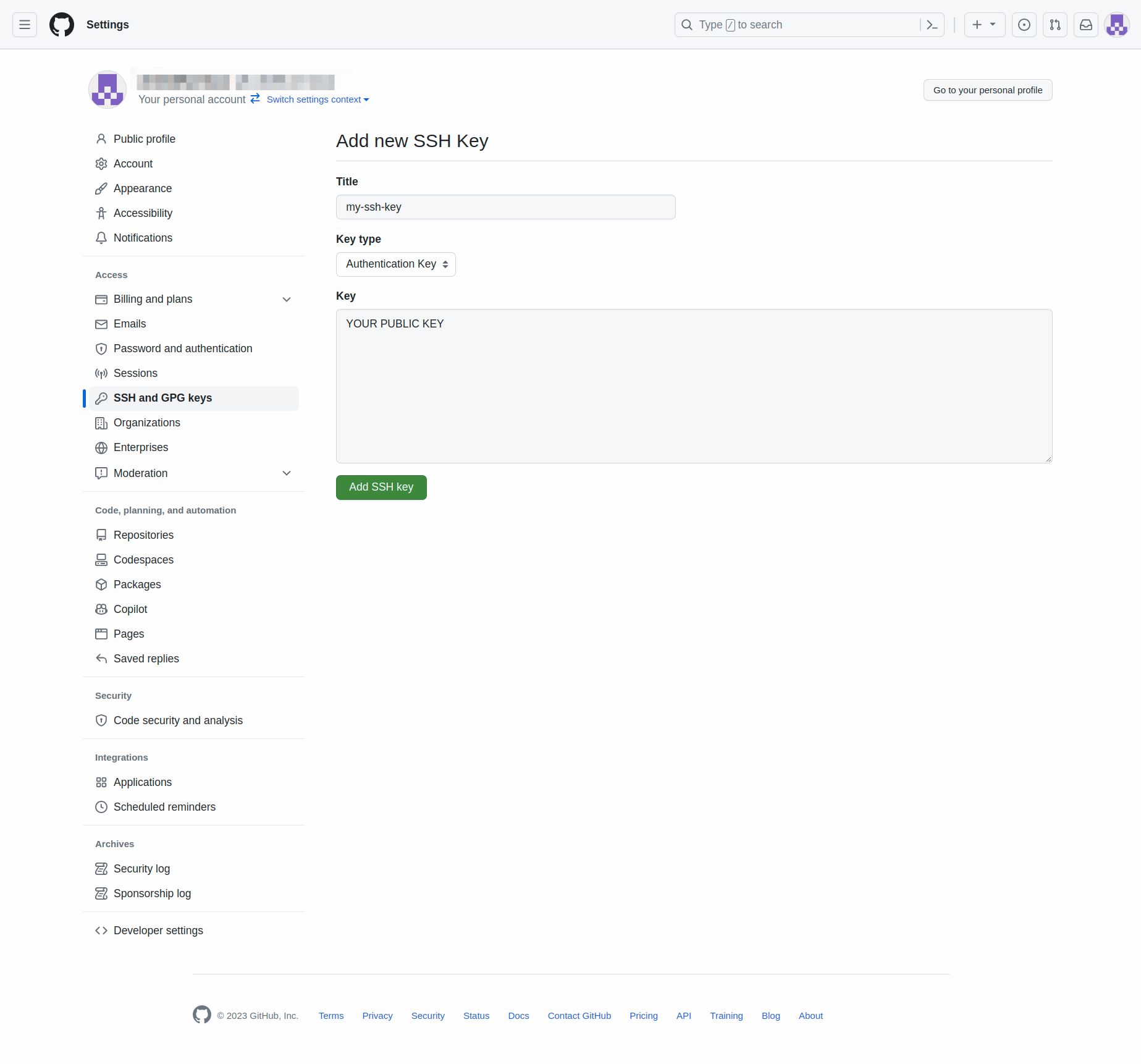
Now add the public key of the keypair you generated earlier.
Adding Private Key to Vault#
Now that we have added the public key to GitHub, let's add the private key to Vault.
-
Access Vault from
Forecastleconsole, searchVaultand open theVaulttile. -
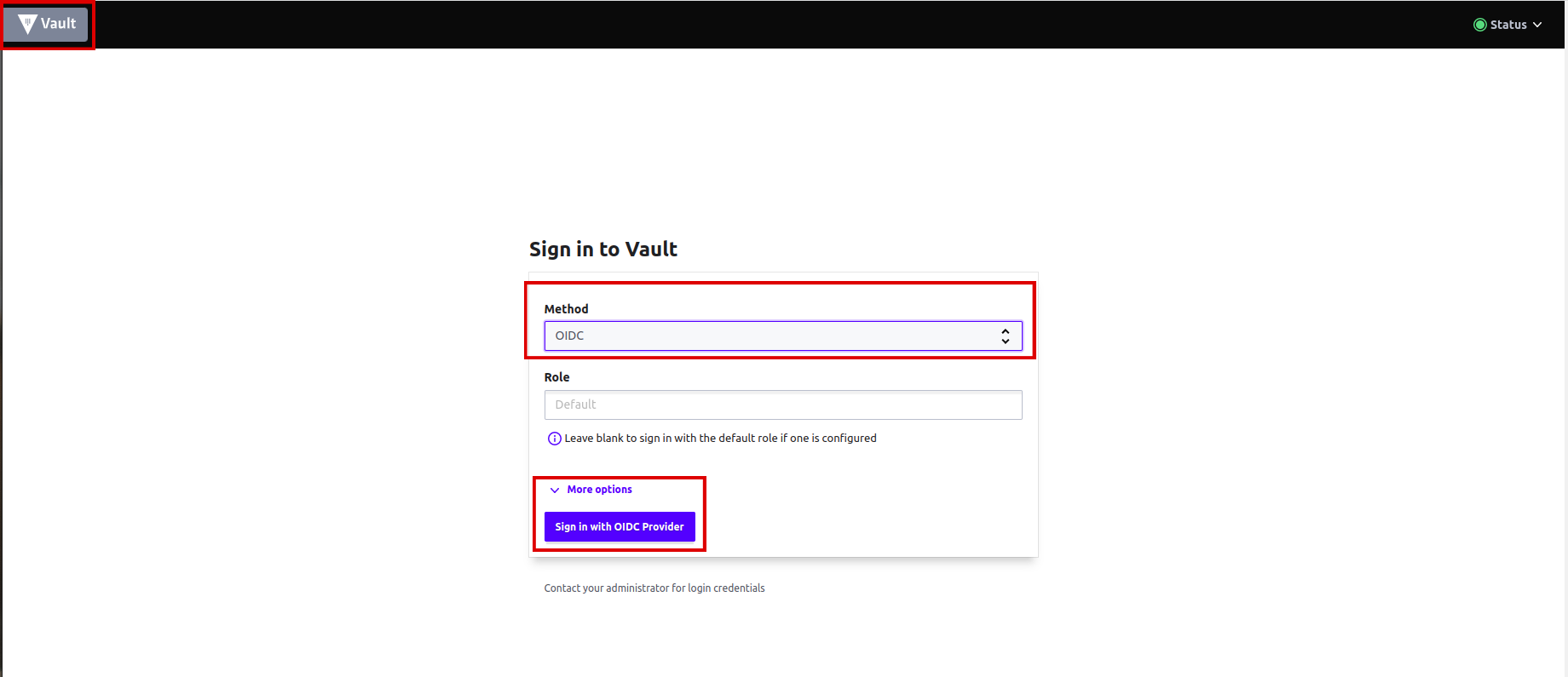
From the drop-down menu under
Method, selectOIDCand click onSign in with OIDC Provider. -
You will be brought to the
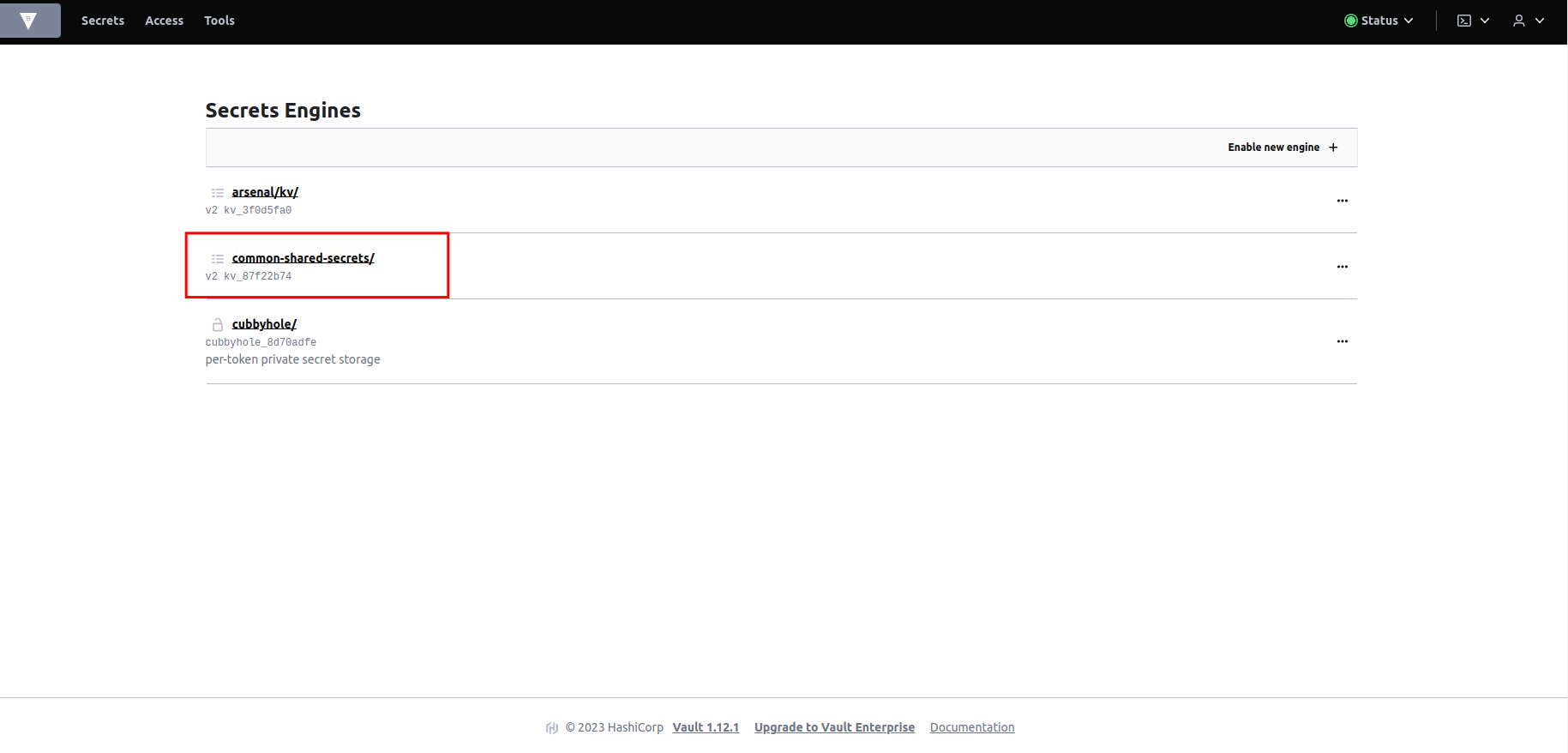
Vaultconsole. You should seecommon-shared-secretsfolder. -
Click on
common-shared-secrets. -
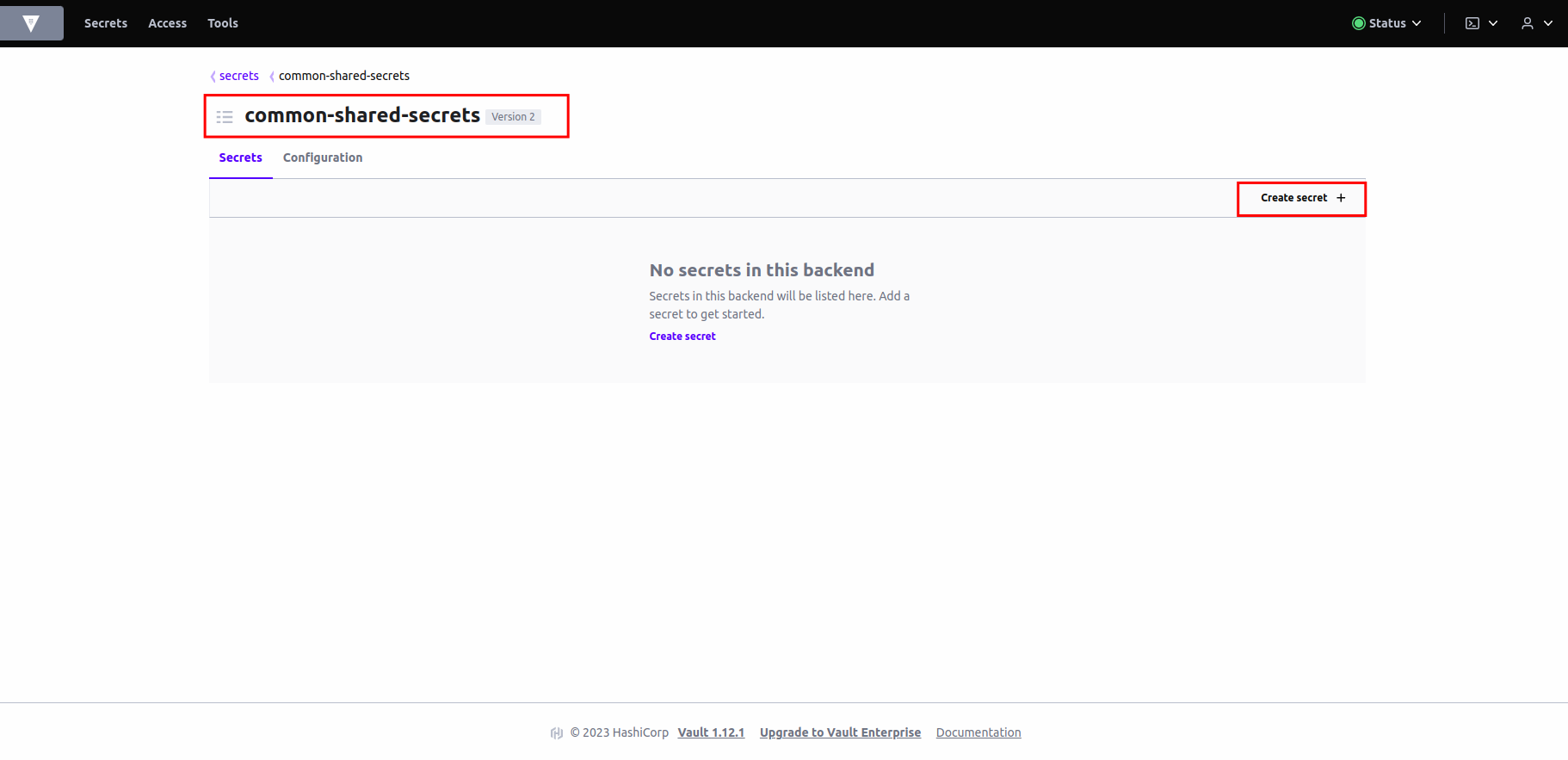
You will now be brought to the
secretsand theconfigurations. Click oncreate secret. -
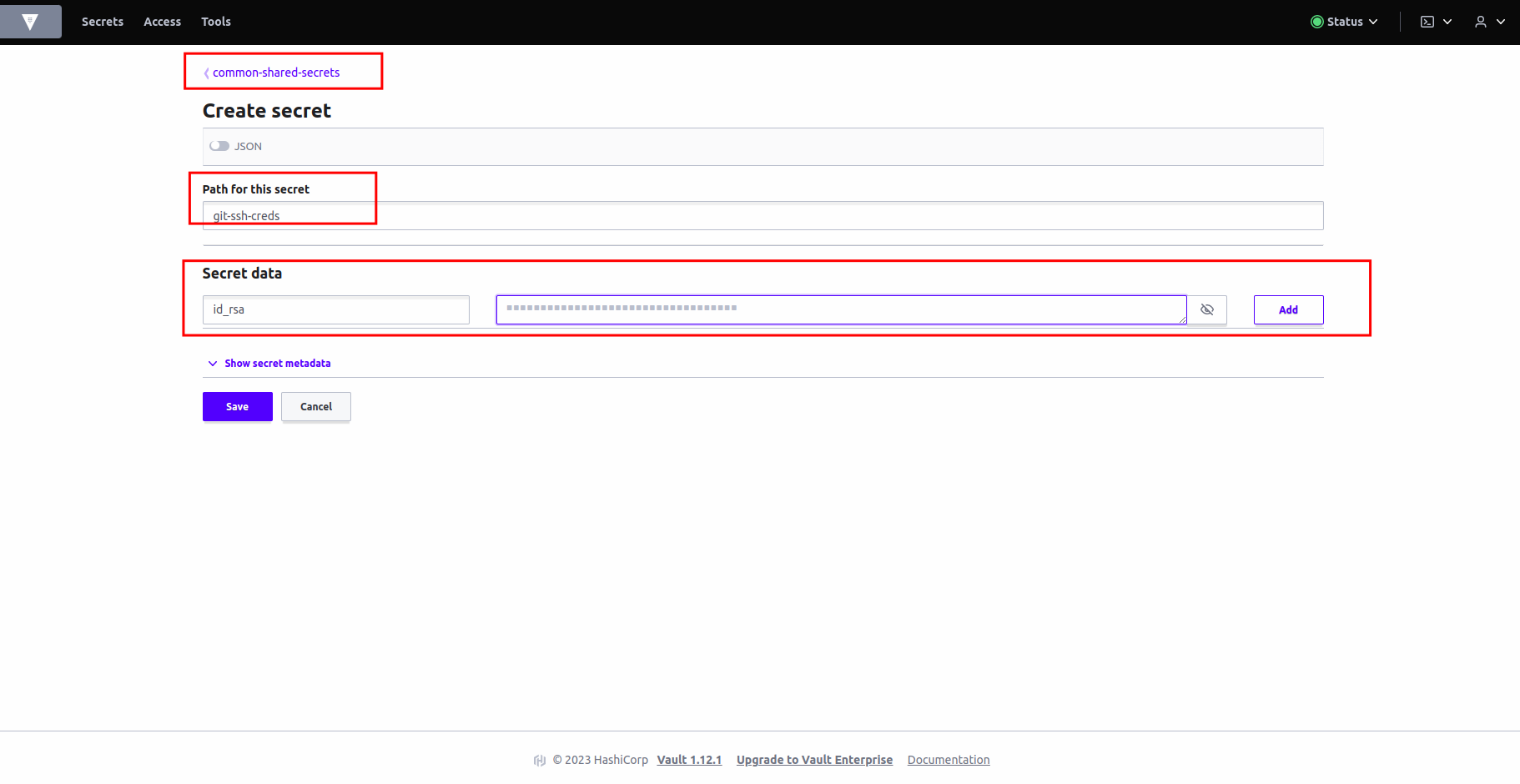
Let's create a
git-ssh-credssecret for our webhook secret. Write the name of the secret inpathwhich isgit-ssh-creds. Addsecret data- key:
id_rsa, value: (The SSH Private Key). Hit save.
- key:
Adding External Secret#
Since we want the git-ssh-creds secret to be deployed in all of the tenant namespaces, we will use a multi-tenant-operator template to deploy it.
-
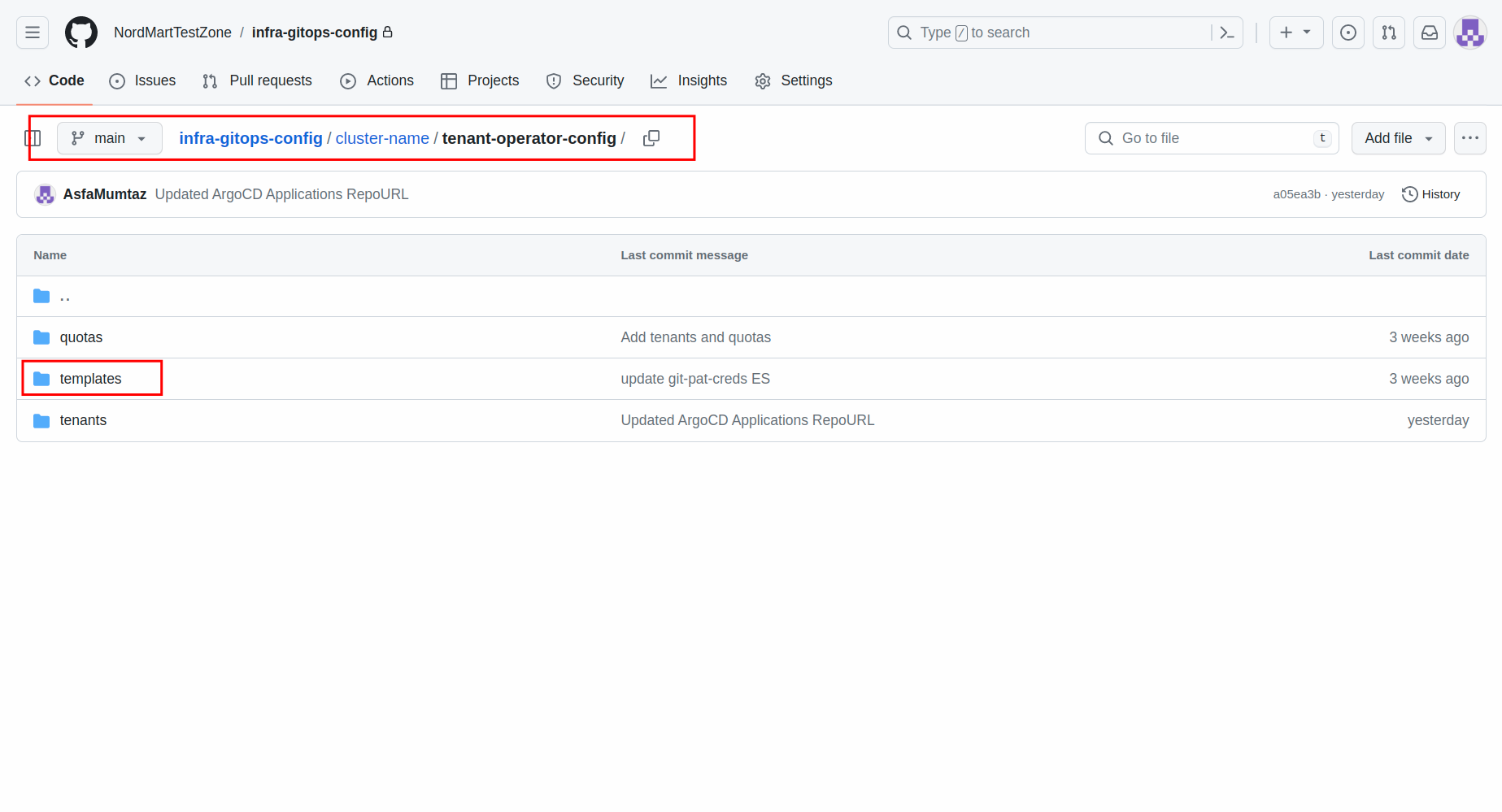
Open up the
infra-gitops-configrepository that we have already bootstrapped. -
Open the
tenant-operator-configfolder and create atemplatesfolder inside it: -
Now create a file named
git-ssh-creds-template.yamland add the following content:apiVersion: tenantoperator.stakater.com/v1alpha1 kind: Template metadata: name: git-ssh-creds resources: manifests: - apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata: name: git-ssh-creds spec: secretStoreRef: name: tenant-vault-secret-store kind: SecretStore refreshInterval: "1m0s" target: name: git-ssh-creds creationPolicy: 'Owner' template: data: id_rsa: "{{ .id_rsa }}" data: - secretKey: id_rsa remoteRef: key: git-ssh-creds property: api_private_key -
Create another file named
git-ssh-creds-tgi.yamland add the following content: