Add Synthetic Monitoring using UptimeRobot#
In this tutorial, we'll guide you through the process of configuring UptimeRobot's Endpoint Monitoring to generate alerts for your application on SAAP based on its availability. Additionally, we'll cover the setup of TLS for secure communication with your application, enhancing data integrity and privacy.
Objectives#
- Enable and configure UptimeRobot's Endpoint Monitoring for your application on SAAP.
- Generate a self-signed TLS certificate and create a TLS secret in SAAP.
- Update the Ingress configuration to include TLS settings for secure communication.
Key Results#
- Successful configuration of UptimeRobot Endpoint Monitoring, implementation of TLS for secure communication for your deployed application.
Tutorial#
Enable Endpoint Monitoring in values.yaml#
- You need to add the following lines to your
deploy/values.yamlfile:
Create a TLS Certificate#
-
Review the
httpssetting in ourapplicationchart template for Endpoint Monitor, you'll find out that thehttpsis true by default. So for that purpose we need to create aTLScertificate.openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=review.<CLUSTER_NAME>.lab.kubeapp.cloud"Note: Add your cluster name in the above route.
Now we have our
TLScertificate andTLSkey. Save it to a path.
Create a TLS Secret#
-
Let's create
TLSsecret on your cluster. Identify the namespace you are using to deploy the application.
Update Ingress Configuration in values.yaml#
-
By default, Endpoint Monitor uses
ingress. As we already have createdTLSsecret, let's modify it by adding theTLSsecret to our ingress configuration. -
Save and run
tilt upat the root of your directory. Hit the space bar and the browser withTILTlogs will be shown. If everything is green then the changes will be deployed on the cluster. -
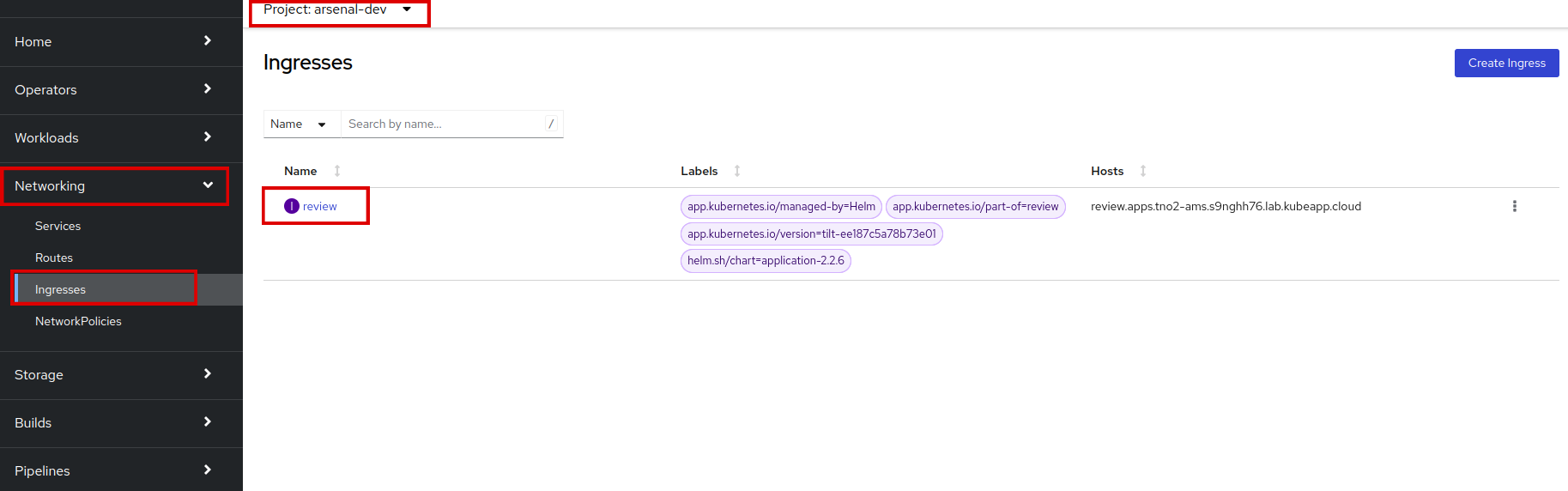
Navigate to SAAP to see our configurations. Let's first check ingress, go to your namespace and then switch to Networking > Ingresses.
Verify that the Ingress is created with the name
review. -
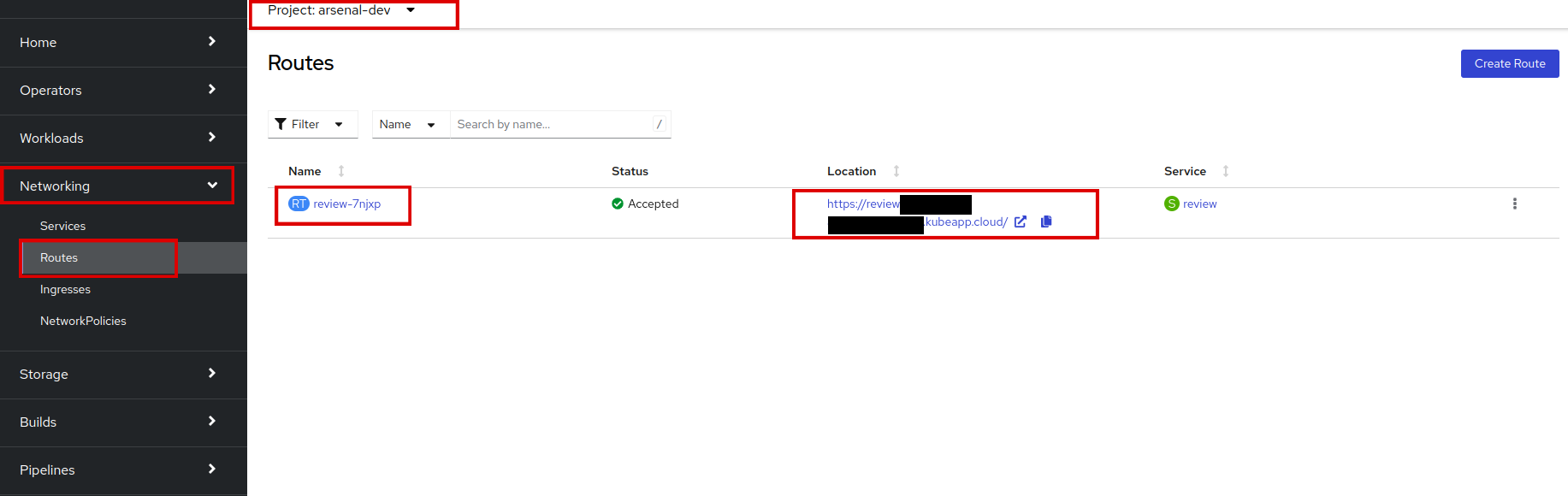
Next, check the Routes. As
TLSis in use, the route should now havehttpsnow. In your namespace, go to Networking > Routes.Confirm that the route has been updated to use
https. -
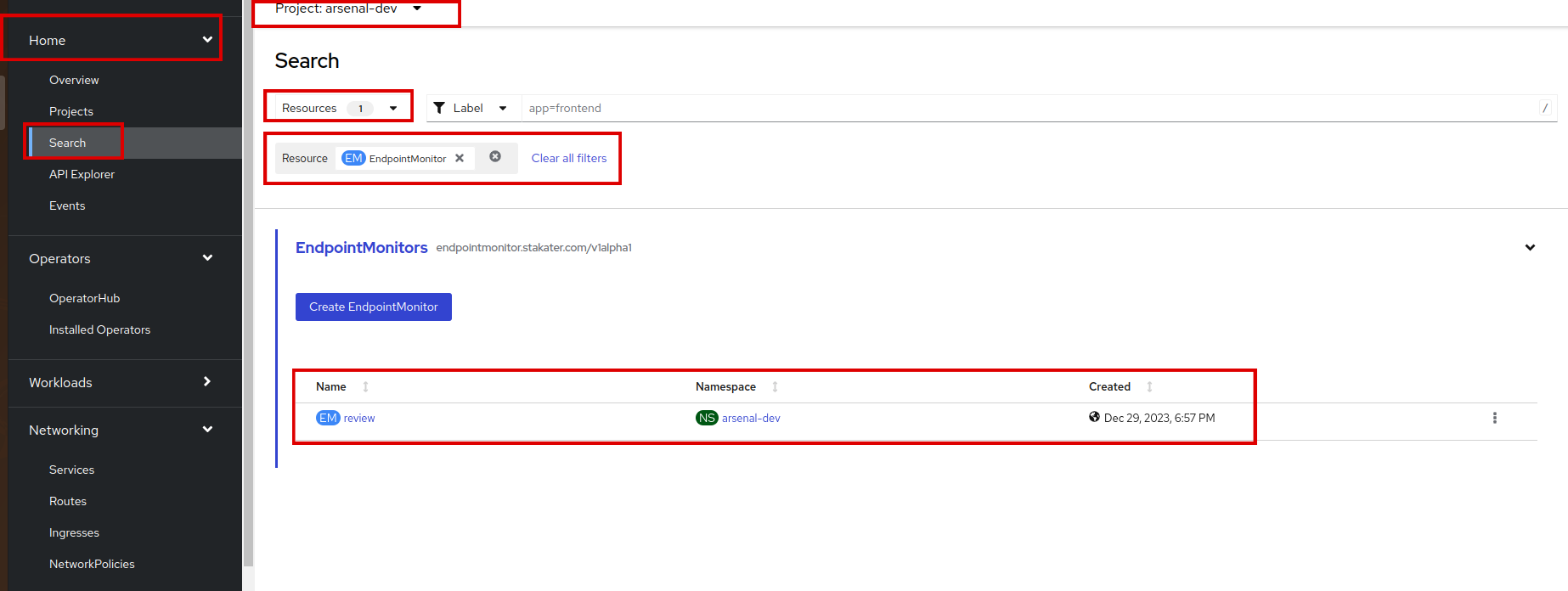
Let's verify our Endpoint Monitor, it should be created by now. Go to Home > Search > Resources, type Endpoint Monitor. If you are in your namespace, you'll see an Endpoint Monitor created there.
We have an
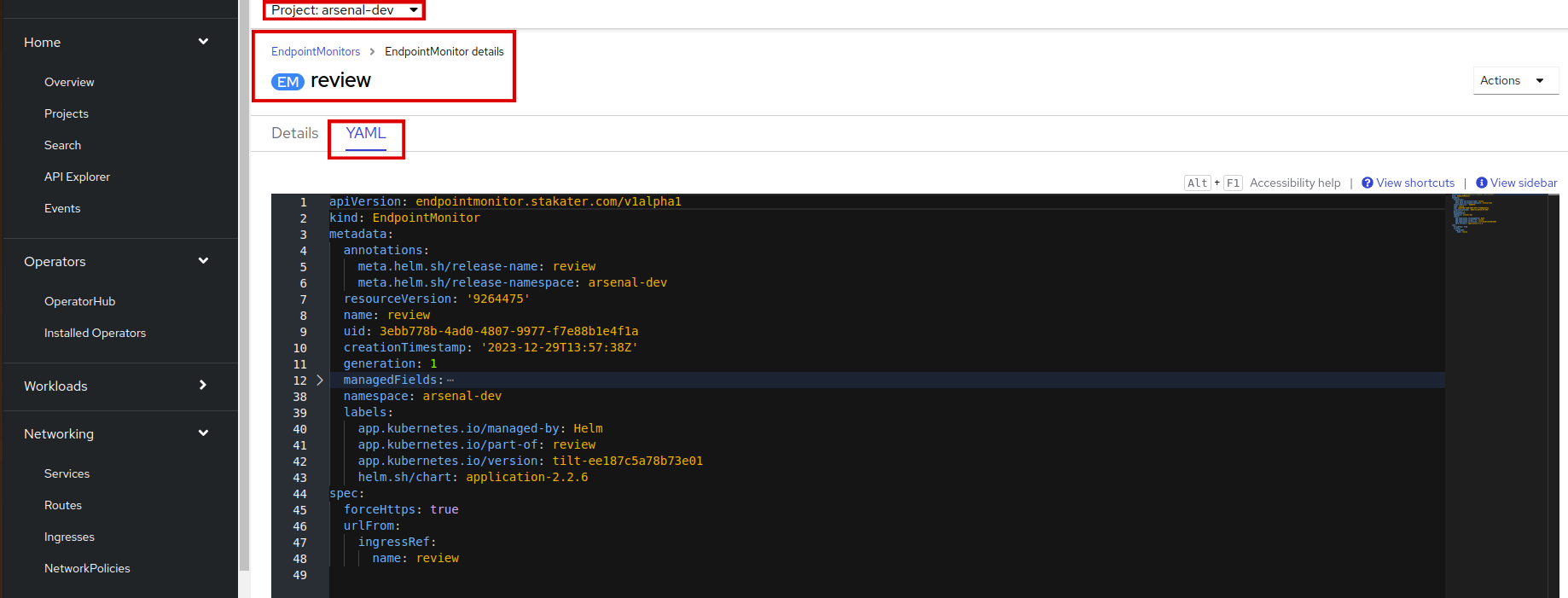
Endpoint Monitorwith the namereview. Awesome!You can also view it's YAML, click on the name and go to
yaml:
Great job! You've successfully configured UptimeRobot Endpoint Monitoring to generate alerts for your SAAP application based on its availability. Now, whenever your application experiences downtime, an alert will be triggered on your UptimeRobot alert contact.